Bybit Hack Explained: How a $1.4 Billion Crypto Heist Unfolded
Key Events of Billion$ Heist
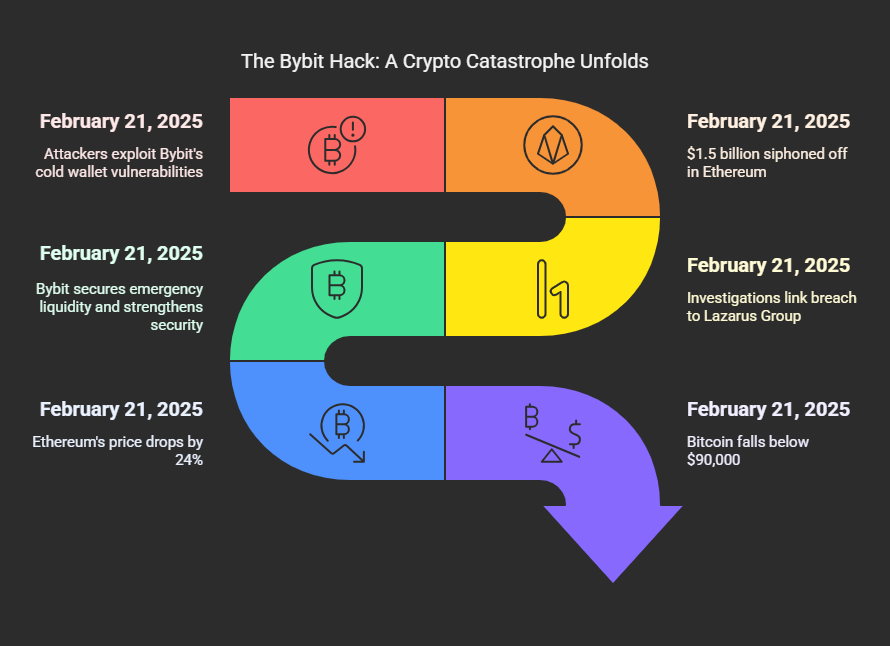
- On Feb. 21, 2025, attackers exploited vulnerabilities in Bybit’s cold wallet infrastructure, siphoning off $1.5 billion in Ethereum in the largest exchange hack to date.
- Investigations linked the breach to North Korea’s Lazarus Group, which used advanced techniques to manipulate transactions and launder stolen funds.
- After Bybit hack, they responded swiftly, securing emergency liquidity, strengthening security measures, and maintaining full solvency to prevent a mass user exodus.
- The hack triggered a 24% drop in Ethereum’s price, pushed Bitcoin below $90,000, and intensified regulatory scrutiny on crypto exchange security.
The Day Crypto Shook: How the Bybit Hack Unfolded
It started like any other day in the control room at Bybit—until it wasn’t. A routine transfer from the exchange’s Ethereum cold wallet suddenly triggered an alert.
Within minutes, millions of dollars in crypto had vanished. By the time the dust settled, over $1.5 billion worth of Ether (ETH) had been siphoned off in what would become one of the largest cryptocurrency heists in history.
The February 2025 Bybit hack was not a random attack but a meticulously planned operation that exposed critical vulnerabilities in even the most secure trading platforms.
The breach exploited weaknesses in transaction approval processes, smart contract logic, and offchain infrastructure.
The aftermath was equally dramatic. Bitcoin (BTC) and ETH prices plummeted, investors panicked, and regulators sharpened their focus on security standards.
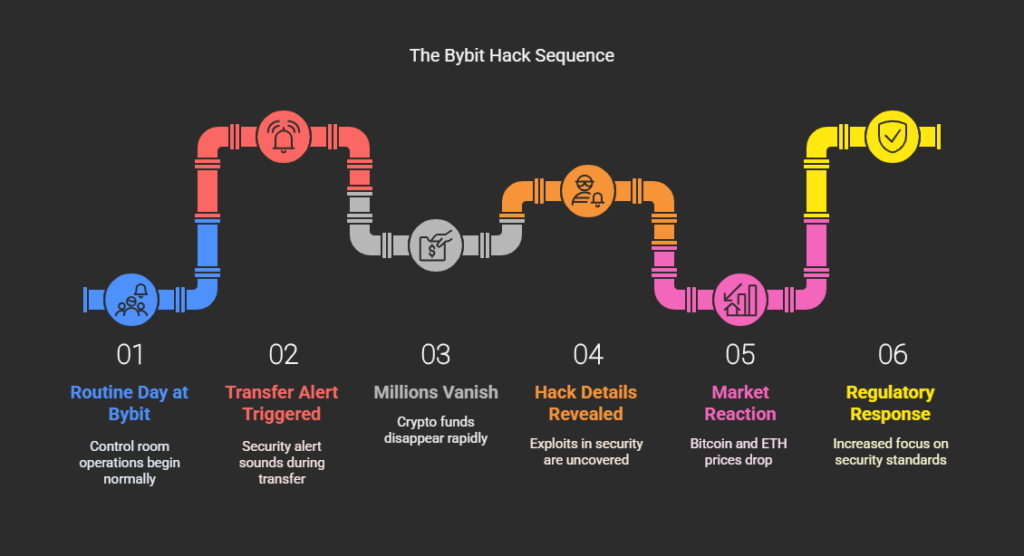
As investigations unfolded, authorities traced the attack back to North Korea’s infamous Lazarus Group, a state-backed cybercrime syndicate with a long history of targeting financial institutions.
This thread unpacks the full story:
1. how the attack happened
2. the tactics used by the hackers.
Prelude to the 2025 Bybit Hack: The Growing Threat
The cryptocurrency industry has always been a high-value target for cybercriminals, but the years leading up to 2025 saw an unprecedented escalation in cyber threats.
In the first half of 2024 alone, the amount of crypto stolen through hacks and exploits more than doubled compared to the same period in 2023.
Why were centralized exchanges like Bybit targeted?
- Large asset holdings: Centralized platforms store billions in user funds, making them an attractive payday for hackers.
- Offchain vulnerabilities: Despite onchain security measures, many exchanges rely on offchain infrastructures that can be exploited.
- Human factor: Cyber adversaries increasingly used social engineering and phishing attacks to target exchange personnel.
Bybit’s Pre-Hack Security Measures
Bybit wasn’t reckless—it had solid security protocols in place:
- Cold Storage: A significant portion of user funds were kept in cold wallets, stored offline to mitigate hacking risks.
- Multisignature Wallets: Transactions required multiple private keys to be authorized, ensuring no single point of failure.
- Regular Security Audits: Bybit conducted periodic assessments to proactively identify system vulnerabilities.
Yet, even the best security setups can be bypassed when facing a determined, state-sponsored hacking group like Lazarus Group.
Timeline of the Bybit Hack: Feb. 21, 2025
So, how did they do it? The attackers executed a highly sophisticated and meticulously planned exploit targeting Bybit’s cold wallet infrastructure. Here’s how it happened, step by step:
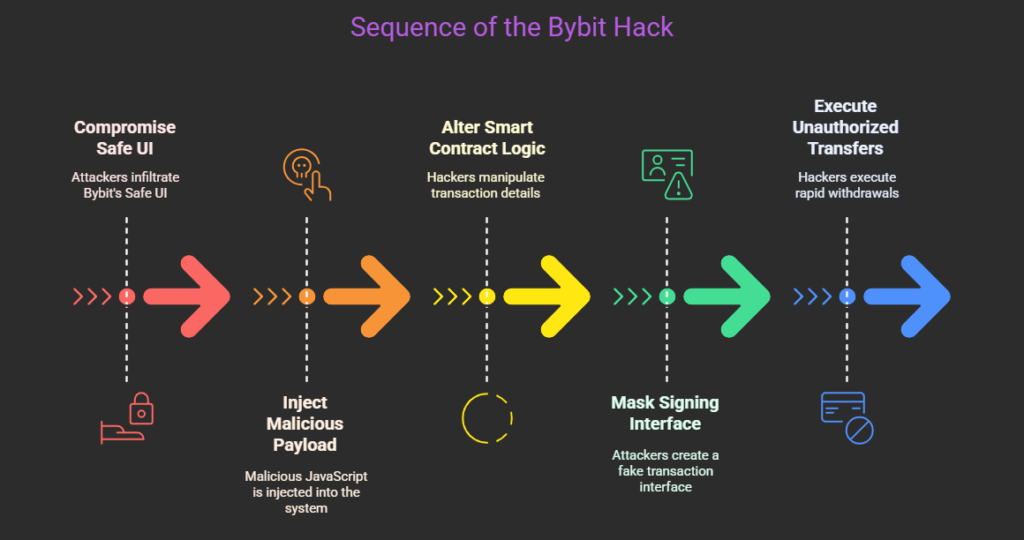
1. Compromising the Safe UI
The attackers infiltrated Bybit’s Safe UI, likely through a supply chain attack or social engineering. They injected a malicious JavaScript payload capable of detecting and modifying outgoing transactions in real time.
2. Altering the Smart Contract Logic
Once inside the UI, the hackers manipulated the transaction details before they were displayed to the signers. They embedded a hidden ‘delegatecall’ instruction, allowing them to upgrade the smart contract logic undetected. Instead of transferring funds to Bybit’s hot wallet, the transactions were redirected to wallets controlled by the attackers.
3. Masking the Signing Interface
To avoid detection, the attackers crafted a legitimate-looking transaction interface for Bybit’s security team. The security personnel believed they were approving routine fund transfers, but in reality, they were unknowingly signing off on a massive heist.
4. Executing the Unauthorized Transfers
Once in control, the hackers initiated multiple rapid withdrawals to various unidentified addresses, making it impossible to track the movement of funds in real time.
💡 Did you know? The stolen funds were quickly converted into Bitcoin and other cryptocurrencies and then dispersed across multiple blockchain addresses—a laundering technique known as “chain hopping” to obscure their origins.
Bybit’s Recovery Efforts: Damage Control and Rebuilding Trust
After the $1.5 billion hack, Bybit had to act fast to prevent a full-blown crisis. Here’s what they did:
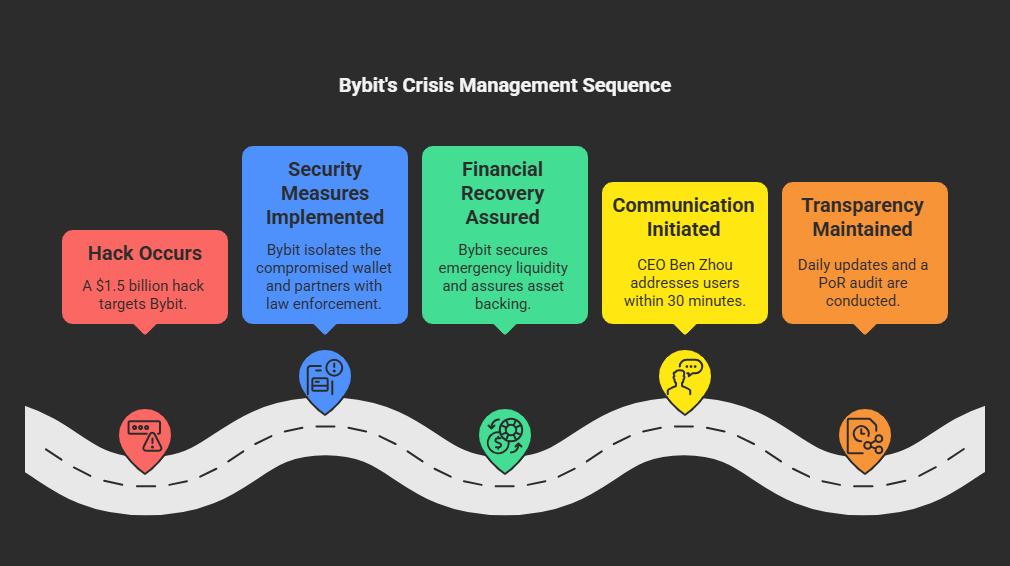
1. Security Measures & Containment
- Isolated the compromised cold wallet and halted unauthorized transactions within minutes.
- Partnered with blockchain analytics firms and law enforcement agencies to trace stolen assets.
- Overhauled multisig security with its wallet provider, Safe, adding stricter manual verification measures.
2. Financial Recovery & Solvency Assurance
- Assured users that all customer assets remained 1:1 backed, preventing mass withdrawals.
- Secured emergency liquidity worth 447,000 ETH ($1.1 billion) from partners like Binance, Bitget, and Galaxy Digital.
- Avoided buying ETH on the open market to prevent further price volatility.
3. Communication & Transparency
- CEO Ben Zhou addressed users within 30 minutes of the breach, hosting a live-streamed Q&A.
- Daily updates were shared on security upgrades and fund recovery.
- A full proof-of-reserves (PoR) audit was conducted on Feb. 24, confirming Bybit’s solvency.
🎯 Bybit’s quick response, financial backing, and transparent communication prevented a total collapse and mass exodus of users.
The Lazarus Group: The Masterminds Behind the Hack
The FBI publicly attributed the attack to the Lazarus Group, North Korea’s state-sponsored cybercrime syndicate. These hackers had already orchestrated some of the biggest crypto heists in history:
- 2022 Ronin Network hack: $620 million stolen
- 2022 Horizon Bridge attack: $100 million stolen
- 2023 Atomic Wallet breach: $100 million stolen
Bybit’s hack followed a familiar pattern: stolen funds were converted into Bitcoin, laundered across multiple blockchains, and cashed out through obscure channels.
The Ripple Effect: Market Impact & Regulatory Crackdown
The Bybit hack shook the entire crypto industry:
- Ethereum dropped 24%, and Bitcoin plunged below $90,000—its lowest price since November 2024.
- Regulators intensified scrutiny on exchanges, calling for stricter security standards.
- Forbes warned that the hack could dent consumer confidence in crypto.
FAQs – Bybit Exchange Hack by The Lazarus Group
1. What caused the Bybit hack?
The hack was caused by vulnerabilities in Bybit’s cold wallet infrastructure, allowing attackers to manipulate transaction approval processes and steal funds.
2. Who was responsible for the Bybit hack?
Investigations linked the attack to North Korea’s Lazarus Group, a state-backed cybercrime syndicate notorious for crypto-related cyber heists.
3. How much was stolen in the Bybit hack?
The attackers siphoned off approximately $1.4 billion in Ethereum, making it one of the largest exchange hacks in history.
4. What steps did Bybit take after the hack?
Bybit quickly secured emergency liquidity, enhanced its security protocols, collaborated with forensic experts, and launched a bounty program to recover stolen funds.
5. How did the hack impact the crypto market?
Ethereum’s price dropped by 24%, Bitcoin fell below $90,000, and the incident intensified regulatory scrutiny on crypto exchange security.
6. Could this happen to other exchanges?
Yes. Even well-secured platforms are vulnerable to advanced cyberattacks. This hack highlights the need for stronger security, proactive monitoring, and industry-wide collaboration.
Read - Why Decentralized over Centralized Wallets
Final Thoughts: The Hard Lesson for Crypto Security
The Bybit hack is a stark reminder that no exchange is immune to highly sophisticated cyber threats. The industry must prioritize security innovation, proactive threat detection, and global cooperation to prevent another catastrophic breach.
In an ecosystem built on trust, the stakes have never been higher.
