Unveiling the Lazarus Group: North Korea’s Team behind Bybit Attack
North Korea’s Lazarus Group has become infamous for executing some of the most sophisticated cyber heists in history. From high-profile exchange hacks to multi-million-dollar DeFi exploits, this state-sponsored hacking collective has stolen billions in crypto to fund North Korea’s illicit activities.
In this article, we break down Lazarus Group’s biggest heists, their evolving tactics, and what the crypto industry can do to counter these threats.
Key Takeaways
- The Lazarus Group is a North Korean state-backed hacking team responsible for billion-dollar cyber heists, funding the country’s missile and nuclear programs.
- They use custom malware, zero-day vulnerabilities, and spear-phishing campaigns to breach financial institutions, cryptocurrency exchanges, and government agencies.
- Notable attacks include the $1.5-billion Bybit hack (2025), the $625-million Ronin Bridge breach (2022), and the $101-million Bangladesh Bank heist (2016).
- They employ misdirection, backdoors, anti-forensic techniques, and wipers to maintain access and conceal their tracks.
Who is the Lazarus Group?
The Lazarus Group is a cybercriminal organization linked to North Korea, conducting some of the most sophisticated financial heists in history.
Since 2017, the group has stolen an estimated $6 billion from the cryptocurrency industry, making it one of the most notorious hacking syndicates worldwide.
State-Sponsored Cybercrime
The Lazarus Group operates under the patronage of North Korea’s Reconnaissance General Bureau (RGB), the nation’s primary intelligence agency.
The U.S. Federal Bureau of Investigation (FBI) has labeled Lazarus as a state-sponsored hacking organization, directly contributing to North Korea’s nuclear and missile programs.
How Does the Lazarus Group Operate?
Advanced Hacking Techniques
The Lazarus Group employs sophisticated tactics, including:
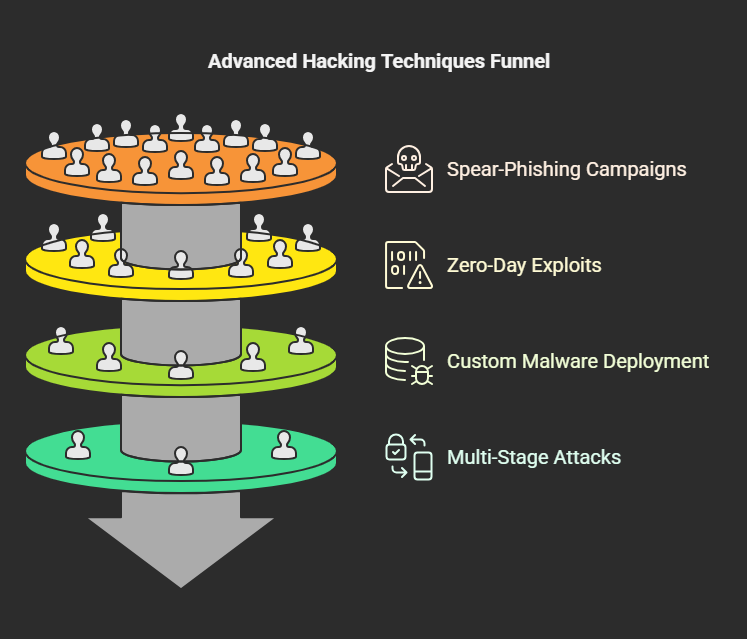
- Custom malware such as MagicRAT and QuiteRAT.
- Zero-day exploits, targeting unknown vulnerabilities.
- Spear-phishing campaigns to gain unauthorized access to corporate networks.
- Multi-stage attacks, including backdoors and data-wiping techniques.
Social Engineering & Exploits
The group manipulates users through social engineering, tricking them into revealing sensitive data. They also exploit weak API security, as seen in the WazirX and Bybit breaches.
Notable Cyber Heists by Lazarus
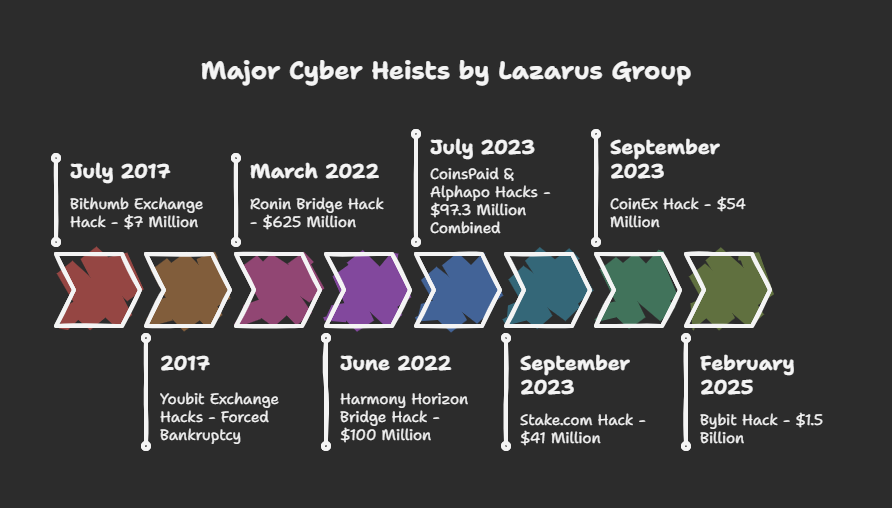
1. Bybit Hack (February 2025) – $1.5 Billion
The biggest crypto heist to date, the Bybit hack targeted the exchange’s SafeWallet interface. The stolen funds were rapidly laundered through multiple wallets.
2. WazirX Hack (July 2024) – $234.9 Million
Lazarus used phishing techniques and API manipulation to breach India’s largest crypto exchange, leading to severe legal and financial repercussions.
3. Stake.com Hack (September 2023) – $41 Million
The group stole private keys, draining millions from the gambling platform across Ethereum, BNB Smart Chain, and Polygon networks.
4. CoinEx Hack (September 2023) – $54 Million
Similar to the Stake.com hack, the CoinEx attack involved unauthorized transactions traced back to Lazarus through blockchain forensics.
5. CoinsPaid & Alphapo (July 2023) – $97.3 Million Combined
The Lazarus Group used fake hiring campaigns and bribery to infiltrate CoinsPaid, while simultaneously executing a $60-million breach at Alphapo.
6. Harmony Horizon Bridge Hack (June 2022) – $100 Million
By compromising multisignature wallets, Lazarus exploited vulnerabilities in Harmony’s cross-chain bridge.
7. Ronin Bridge Hack (March 2022) – $625 Million
Using malware-infected job offers, they compromised validator keys, executing one of the largest blockchain heists in history.
8. Atomic Wallet Attacks (2022) – $35-$100 Million
Lazarus used custom malware to drain decentralized wallets across multiple accounts.
9. Bithumb Exchange Hack (July 2017) – $7 Million
One of the earliest Lazarus crypto heists, achieved through spear-phishing attacks.
10. Youbit Exchange Hacks (2017) – Forced Bankruptcy
The group hit South Korea’s Youbit exchange twice, leading to the platform’s financial collapse.
Major Cyber Heists That Shook the Digital World
Cybersecurity breaches have become increasingly sophisticated, leading to some of the most infamous heists in history. From crippling ransomware attacks to large-scale financial thefts, these incidents highlight the vulnerabilities within global digital infrastructure. Here’s a look at some of the most significant cyber heists:
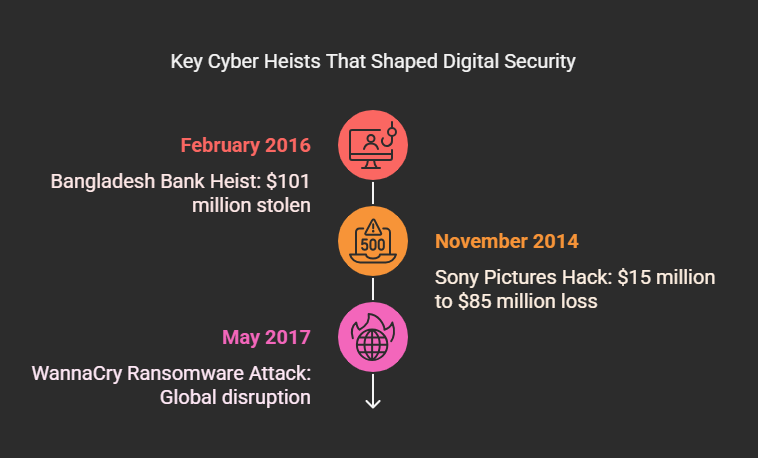
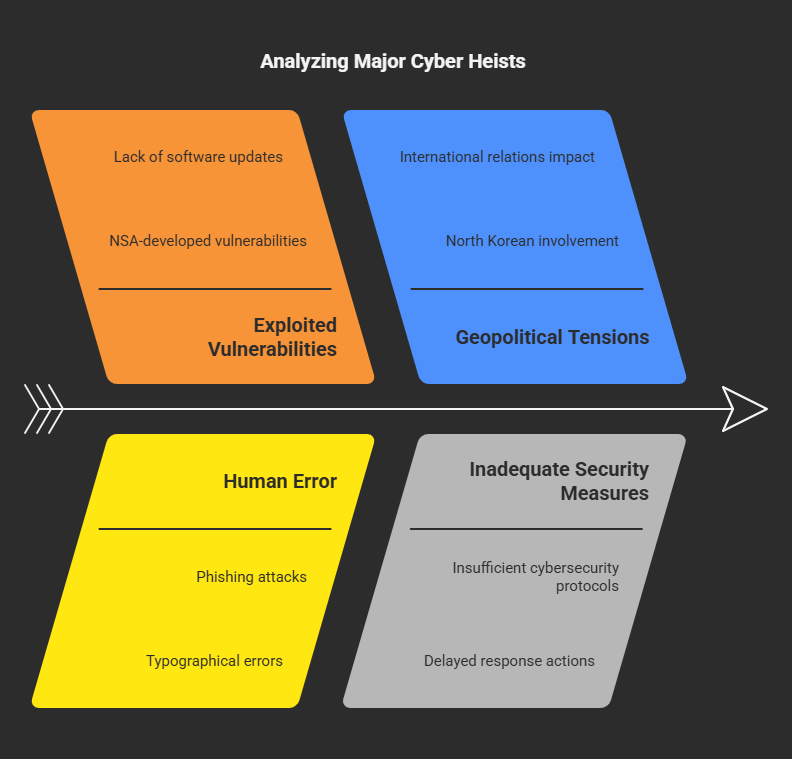
1. WannaCry Ransomware Attack (May 2017)
The WannaCry ransomware attack was a worldwide cybersecurity disaster, infecting over 200,000 computers across 150+ countries. Major organizations like FedEx, Honda, Nissan, and the UK’s National Health Service (NHS) faced severe disruptions, with the NHS even having to reroute ambulances.
The attack exploited an NSA-developed vulnerability, EternalBlue, which was leaked by the hacking group Shadow Brokers. While a security researcher discovered a “kill switch” that temporarily halted the spread, many victims remained locked out of their systems unless they paid the ransom. WannaCry served as a wake-up call for the importance of regular software updates and stronger cybersecurity measures.
2. Bangladesh Bank Heist (February 2016)
One of the biggest cyber thefts in history, the Bangladesh Bank heist, saw attackers attempt to steal nearly $1 billion from the bank’s account at the Federal Reserve Bank of New York. The attack, later attributed to the Lazarus Group, began with a phishing email in 2015 that allowed hackers to infiltrate the bank’s systems.
The perpetrators studied the bank’s operations for months before executing 35 fraudulent transfer requests through the SWIFT banking network. While most were blocked, $101 million was successfully transferred, with $81 million disappearing into accounts in the Philippines. A simple typographical error in one transfer request raised suspicion, preventing further losses.
3. Sony Pictures Hack (November 2014)
Sony Pictures fell victim to a devastating cyberattack by the Guardians of Peace, a group linked to the Lazarus Group. The attackers infiltrated Sony’s network, stealing unreleased films, sensitive employee data, and confidential communications. They also deployed malware that rendered 70% of Sony’s computers unusable.
The breach, reportedly costing Sony between $15 million and $85 million, was allegedly a response to the studio’s planned release of The Interview, a satirical film about the assassination of North Korean leader Kim Jong-un. The US government formally attributed the attack to North Korean-linked hackers, showcasing the growing intersection of cybercrime and geopolitics.
Did You Know? In August 2024, blockchain investigator ZachXBT revealed that 21 North Korean developers had infiltrated crypto startups, collectively earning $500,000 per month. This highlights how cybercriminal networks continue to evolve, exploiting digital finance for illicit gains.
How Crypto Organizations Can Combat Lazarus Group Attacks
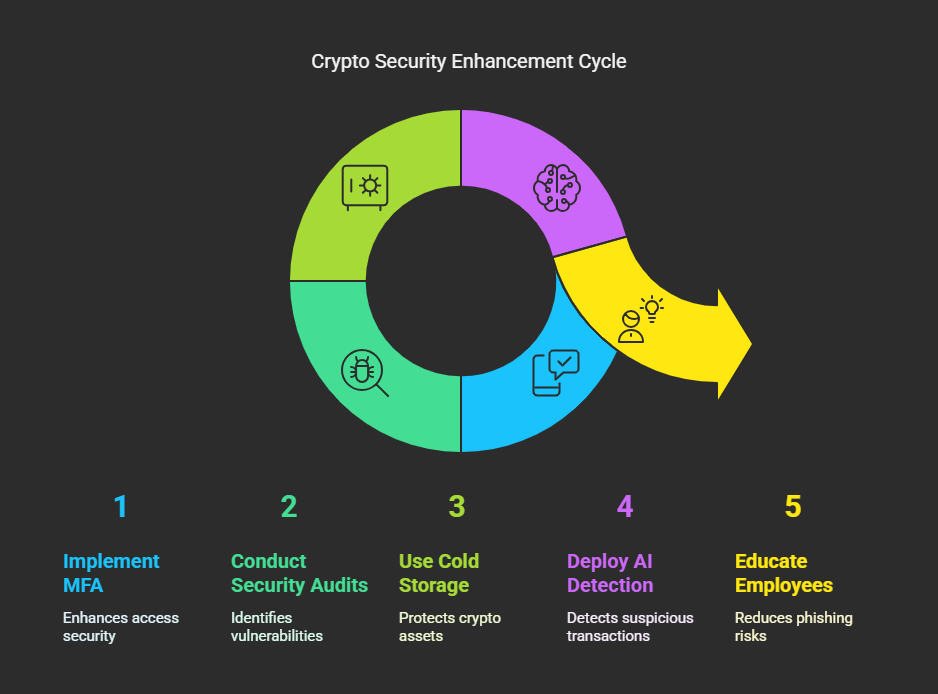
Implement Strong Security Measures
- Multi-factor authentication (MFA) for critical operations.
- Regular security audits to identify vulnerabilities.
- Cold storage for storing large reserves of crypto assets.
Deploy AI-Powered Threat Detection
Advanced AI systems can detect suspicious transactions and prevent fraud before funds are drained.
Educate Employees on Phishing Attacks
Companies should train employees to recognize and avoid phishing attempts, reducing the risk of social engineering-based breaches.
Conclusion
The Lazarus Group remains one of the biggest cybersecurity threats, continually evolving its attack methods. The growing number of crypto heists highlights the need for exchanges and financial institutions to prioritize security to mitigate future attacks.
Read - BlackRock adds BTC to 150$ Model Portfolio
FAQs on the Lazarus Group Hacking
1. Who is the Lazarus Group?
The Lazarus Group is a cybercriminal organization widely believed to be linked to North Korea. It is responsible for some of the most notorious cyberattacks, including financial thefts, ransomware attacks, and espionage.
2. What are some of the biggest cyberattacks attributed to the Lazarus Group?
Some major cyberattacks linked to the Lazarus Group include:
- Bangladesh Bank Heist (2016): Stole $101 million through fraudulent SWIFT transactions.
- Sony Pictures Hack (2014): Breached Sony’s network, leaking confidential data and causing millions in damages.
- WannaCry Ransomware Attack (2017): Affected 200,000+ computers worldwide using a stolen NSA exploit.
- Axie Infinity’s Ronin Bridge Hack (2022): Stole over $620 million in crypto, one of the biggest DeFi hacks.
3. How does the Lazarus Group operate?
The Lazarus Group uses sophisticated phishing campaigns, malware attacks, and exploits vulnerabilities in financial and corporate systems. It often targets cryptocurrency exchanges, banks, and government agencies to fund North Korea’s activities.
4. What are the Lazarus Group’s main targets?
The group primarily targets:
- Financial institutions (banks, crypto exchanges)
- Government organizations
- Large corporations (tech, entertainment, healthcare)
- Defense and military sectors
5. How did the Lazarus Group steal millions from the Bangladesh Bank?
They infiltrated the SWIFT banking system through a malware-infected email, studied the bank’s operations, and attempted to transfer nearly $1 billion to offshore accounts. A typo in one request raised red flags, preventing the full heist.
6. What was the impact of the Sony Pictures hack?
The attack leaked confidential emails, unreleased movies, and personal data of employees. It also destroyed 70% of Sony’s computer network, costing the company millions in damages and delaying major film releases.
7. How does the Lazarus Group target cryptocurrency platforms?
- Fake job offers to trick developers into installing malware
- Social engineering to gain access to company systems
- Exploits in smart contracts to drain funds from DeFi platforms
8. How can individuals and companies protect themselves from Lazarus Group attacks?
- Keep software updated to patch security vulnerabilities
- Use multi-factor authentication (MFA) for sensitive accounts
- Be cautious of phishing emails and fake job offers
- Regularly monitor and secure cryptocurrency wallets
- Employ advanced cybersecurity tools to detect and prevent breaches
9. Has any action been taken against the Lazarus Group?
Yes. The U.S. government has imposed sanctions on individuals linked to the group. Law enforcement agencies worldwide are actively tracking their activities, but the group remains highly elusive and continues to operate under different aliases.
10. Why is North Korea linked to the Lazarus Group?
Cybersecurity experts and intelligence agencies believe the North Korean government sponsors the Lazarus Group to fund its regime amid international sanctions. The stolen funds allegedly support North Korea’s nuclear and military programs.
